The COVID-19 crisis has sent workers and businesses scrambling to setup work-from-home systems and protocols, and with such a rapid migration to remote work it is no surprise technical and security issues have emerged. Here we're going to discuss "Zoombombing"--what it is and how to prevent it.
Read MoreOur Blog
Tags: privacy, Security, internet security, remote work, working from home, Internet Privacy, zoom, COVID-19
What is two-factor authentication (2FA)? And why you REALLY should use it
Posted by Chris Allard on Tue, Apr 07, 2020
The concept is simple, you prove who you are when logging into your accounts by proving two things: something you know (your password) and something you possess (your smartphone, as an example). A lot of users have caught on to two-factor authentication (AKA multi-factor authentication, or abbreviated as MFA or 2FA) and it's adding a ton of security to an inherently insecure internet.
Read MoreTags: privacy, Security, internet security, remote work, encryption, 2FA, Multifactor authentication, 2-factor authentication, MFA
Network Security: How can I keep my printers from being hacked?
Posted by Chris Allard on Mon, Mar 16, 2015
Why would a hacker want my printer?
Networked printer security is often an overlooked security vulnerability area and being overlooked is what a hacker with malicious intent (we'll call them "black hats" here) looks for when wanting to penetrate a network or subnet.Read More
Tags: Hacking, wireless security, Hackers, Security
 THE CLOUD:
THE CLOUD:
By now most of us have a basic understanding of what the cloud is or at least
the core concept. Recently cloud computing has come under fire for its vulnerability to hacks. The technology is sound and lives up to its functionality, that is not the issue.
Tags: cloud, Security, online storage, byod, cloud management

Ok, it's apparent that many of our customers who bring in their computers do in fact have programs that either contain or deploy malicious code with the ability to do a whole range of nasty things. Below is a list of some of the apllications you should delete right now.
Tags: Pop-up Ads, Antivirus, Chrome, Firefox, Web Browser, Browser Hijacking, Security
 The Nuclear Exploit Kit
The Nuclear Exploit Kit
Recently there has been a new piece of malicious code floating around otherwise known as the Nuclear exploit kit. This kit has been deployed by a number of travel websites that have been compromised. It was discovered by security researchers Proofpoint after customers had received promotional emails from legitimate businesses whose emails they had signed up to receive. These emails contained links to the infected websites.
Tags: email, Virus, Browser Hijacking, Security, Malware Prevention
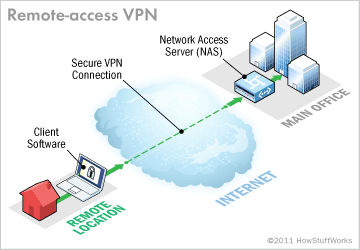
What Is a VPN?
VPN stands for Virtual Private Network. It is a network that uses public networks i.e the internet to connect to remote sites or users together. It encrypts the data making it one of the most secure ways for businesses to communicate remotely or otherwise.
Tags: Anonymity, Security, VPN, Internet, Access, NordVPN, ExpressVPN,, ProtonVPN, Private Internet Access,
If you have the Cryptolocker virus you have 2 weeks to fix it!
Posted by Henry Dallow on Fri, Jun 06, 2014
What Is Cryptolocker?
Cryptolocker is ransomware: malicious software which holds your files to ransom.
So How did I get it? Cryptolocker is spread through infected attachments to emails, or as a secondary infection on computers which are already affected by viruses which offer a back door for further attacks.
Tags: Windows XP, Viruses, Antivirus, Kaspersky, Windows 8, Security, Windows 7
 4 Ways to Keep Your Computer Safe from Viruses
4 Ways to Keep Your Computer Safe from Viruses
If you are anything like many of our customers at Northampton Computer Repair, you worry a lot about your computer catching a nasty virus. While it’s true that the internet is full of viral menace, it doesn’t have to feel like an overwhelming or unavoidable thing. There are things that you as a user should do to reduce your chances of contracting a virus on your home computer or laptop – or rather, things that you should not do.
Tags: Computer Protection, Safe Practices, email, Virus, Security, Malware Prevention, Computer, virus alert
To securely set up your email account in Outlook 2010, begin by thinking about which type of email service you want to use. The 2 main options are POP3 (Post Office Protocol) or IMAP (Internet Message Access Protocol), the differences being that one (IMAP) interacts with the server in real-time and all messages remain on the server and are synced immediately (or at set intervals) with your computer, the other (POP) downloads all of the messages to your computer and when something is changed on your computer, like being read or deleted, the changes are "pushed" back onto the server at set intervals.
Tags: Outlook 2010, Email Setup in Outlook 2010, email, Windows Tips, Security, Customize Windows



 4 Ways to Keep Your Computer Safe from Viruses
4 Ways to Keep Your Computer Safe from Viruses

